Zaraza bot, a novel credential-stealing malware, is being offered for sale on Telegram, which is also being used as a command-and-control (C2) server.
“Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors,” the cybersecurity firm Uptycs said in a report published last week.
“After infecting a computer, the malware retrieves sensitive data and sends it to a Telegram server, where attackers can access it immediately.”
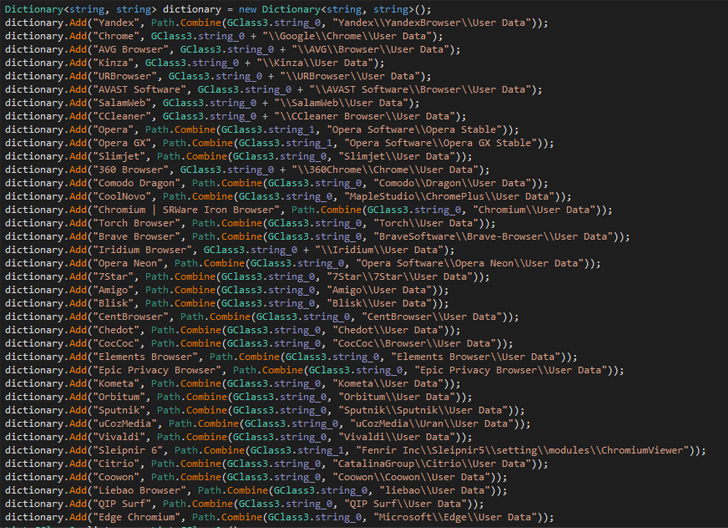
Zaraza bot is designed to target as many as 38 distinct web browsers, including Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, Vivaldi, and Yandex. Zaraza bot is a 64-bit binary file that was compiled using C#. Additionally, it can capture screenshots of the active window.
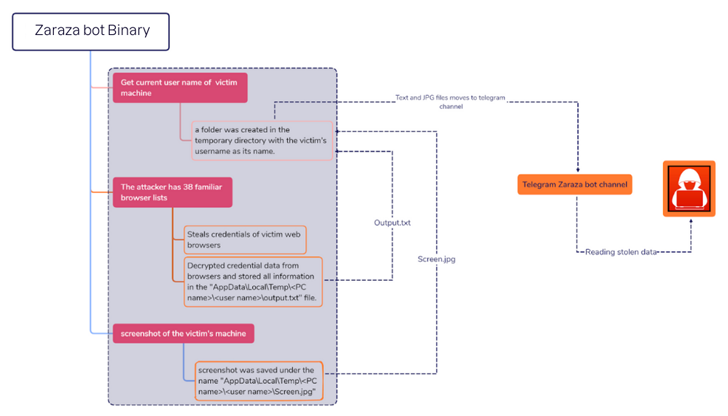
It is the most recent instance of malware capable of stealing logon credentials for online bank accounts, cryptocurrency wallets, email accounts, and other websites deemed valuable by their operators.
Theft of credentials poses a significant threat because it enables threat actors to not only obtain illicit access to victims’ accounts but also to commit identity theft and financial fraud.
According to evidence compiled by Uptycs, Zaraza malware is offered to other cybercriminals as a subscription-based commercial tool. It is presently unclear how the malware spreads, but in the past, information thieves have typically employed multiple techniques, such as malvertising and social engineering.
eSentire’s Threat Response Unit (TRU) disclosed a GuLoader (aka CloudEyE) campaign that targeted the financial sector through phishing emails using tax-themed lures to deliver information stealers and remote access trojans (RATs) such as Remcos RAT.
New Zaraza Bot Credential-Stealer Sold on Telegram Targets 38 Web Browsers
The development follows an increase in malvertising and search engine poisoning techniques to disseminate a growing number of malware families by luring users searching for legitimate applications to download phony installers with stealer payloads.
In a new analysis, the Russian cybersecurity firm Kaspersky found that trojanized pirated software downloaded from BitTorrent or OneDrive is used to deploy CueMiner, a.NET-based downloader that functions as a conduit to install a cryptocurrency miner known as SilentCryptoMiner.
It is recommended that users enable two-factor authentication (2FA) and implement software and operating system updates as soon as they become available to mitigate risks posed by stealer malware.

