Although a virus is the most well-known type of malicious software, there are a few others that can be harmful to your data and devices.
Viruses, worms, and Trojans are three categories of malicious software (malware) that are capable of causing damage to computer systems and networks. Although they all fall under the category of malware, their characteristics and operations are distinct. Here, we discuss the distinctions between viruses, worms, and Trojans, as well as the dangers they pose to your devices.
What are viruses?

A computer virus is a variety of malware that replicates itself by attaching itself to a legitimate program or file. The virus is activated when the infected program or file is executed, and it can propagate to other programs and files on the computer or network. A virus’s primary objective is to replicate and propagate, wreaking havoc on the infected computer or network.
Through email attachments, infected websites, and file-sharing networks, viruses can propagate.
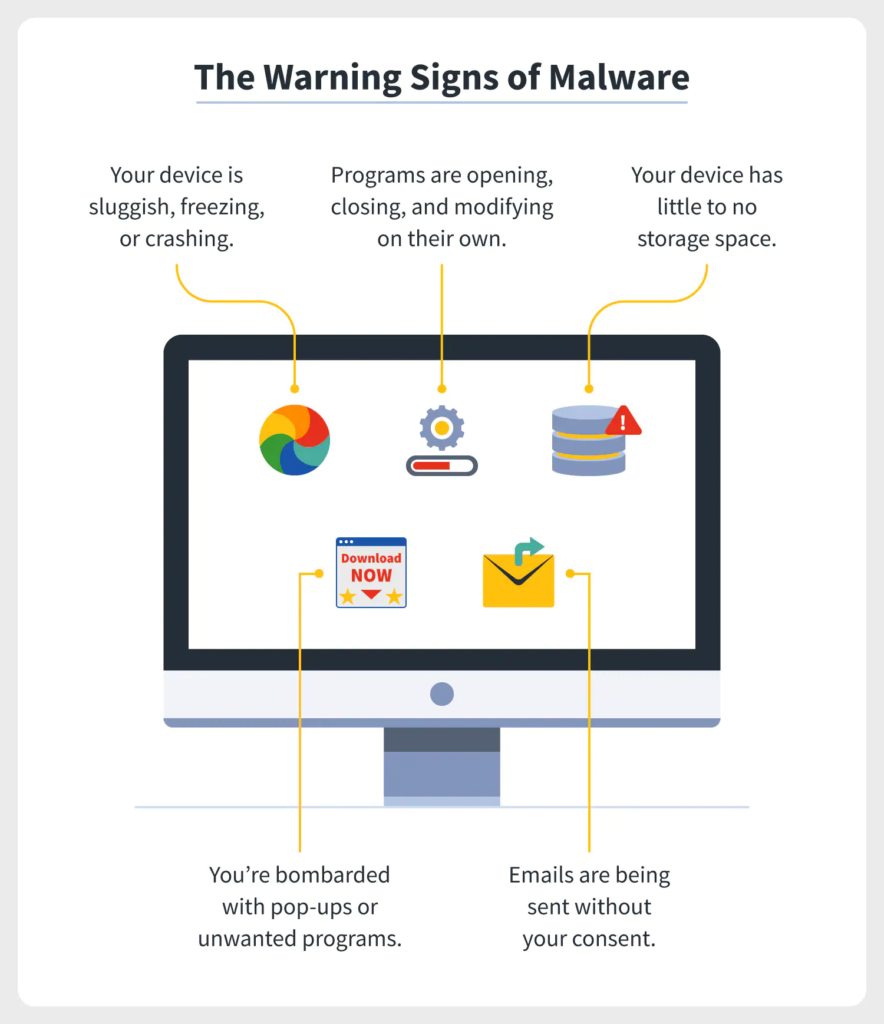
A virus can cause a variety of issues, including a decrease in computer performance, file corruption, and the deletion of vital data. In certain instances, a virus can also grant criminals access to an infected computer, granting them access to sensitive data and personal information.
What is an insect?

A worm is a form of malware designed to propagate rapidly through a network by exploiting security vulnerabilities. Unlike a virus, a worm can propagate without attaching itself to a program or file. Instead, it can replicate and propagate from computer to computer, frequently without the knowledge of the user.
Worms can propagate swiftly and cause extensive harm to computer networks, sometimes resulting in the failure of entire systems. They can also be used to install additional forms of malware, such as spyware or keyloggers, on a computer that has been compromised. Worms can propagate via email, instant messaging, and software and operating system security vulnerabilities.
What exactly is a trojan?

A trojan, or trojan horse, is a variety of malicious software that masquerades as a legitimate application or file. Once the user installs or executes the trojan, it is capable of performing a variety of malicious actions, such as obtaining data, modifying files, and installing additional malware.
Through email attachments, infected websites, and software installations, Trojans can propagate. They are frequently employed in targeted attacks in which the perpetrator seeks access to specific systems or sensitive data.
How are these malware varieties dangerous?
All three varieties of malware are perilous and can cause serious damage to computer systems and networks. Viruses, worms, and Trojans can cause numerous issues, such as:
- Malware can use up system resources and slow down the computer’s performance by consuming system resources.
- Malware can corrupt files and render them inaccessible, resulting in data loss and other issues.
- Theft of data: Malware is capable of stealing sensitive data, such as passwords, credit card numbers, and personal information.
- Malware can be used to install additional malware, such as spyware or keyloggers, on an infected computer.
- Malware can enable criminals to obtain access to the infected computer, granting them access to sensitive data and personal information.